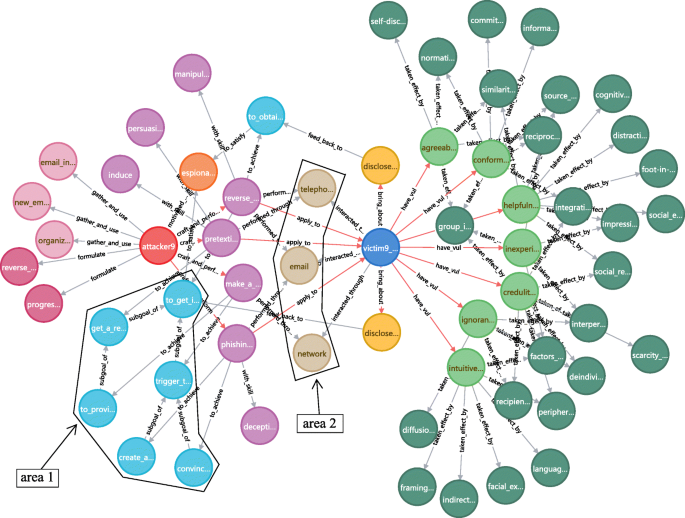

Cybersecurity Scenarios
Network Gate provides a Cybersecurity-based threat vector scenarios including ransomware, insider threats, phishing, and Industrial Control System compromise. Each of these scenarios is unique, so Network Gate only provides templates that can be adapted to your business environment.
Cybersecurity Scenarios
These CTEPs include cybersecurity-based scenarios that incorporate various cyber threat vectors.
Cyber-Physical Convergence Scenarios
Physical impacts resulting from a cyber threat vector.



