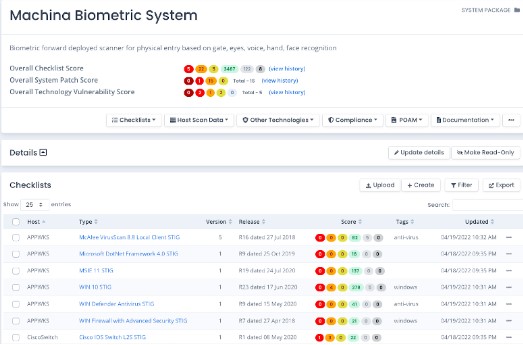
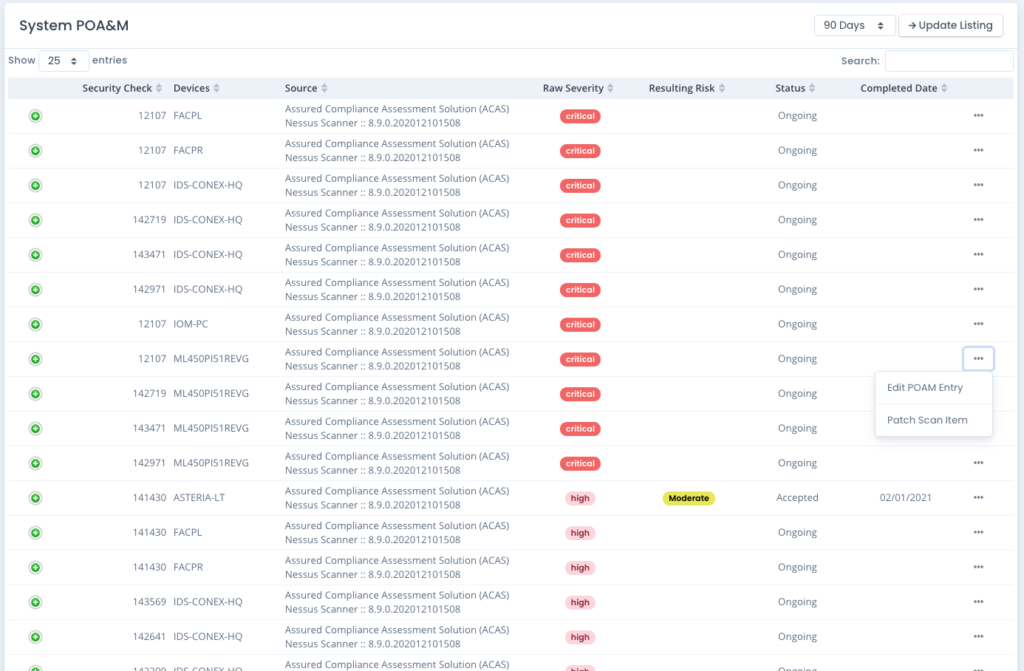
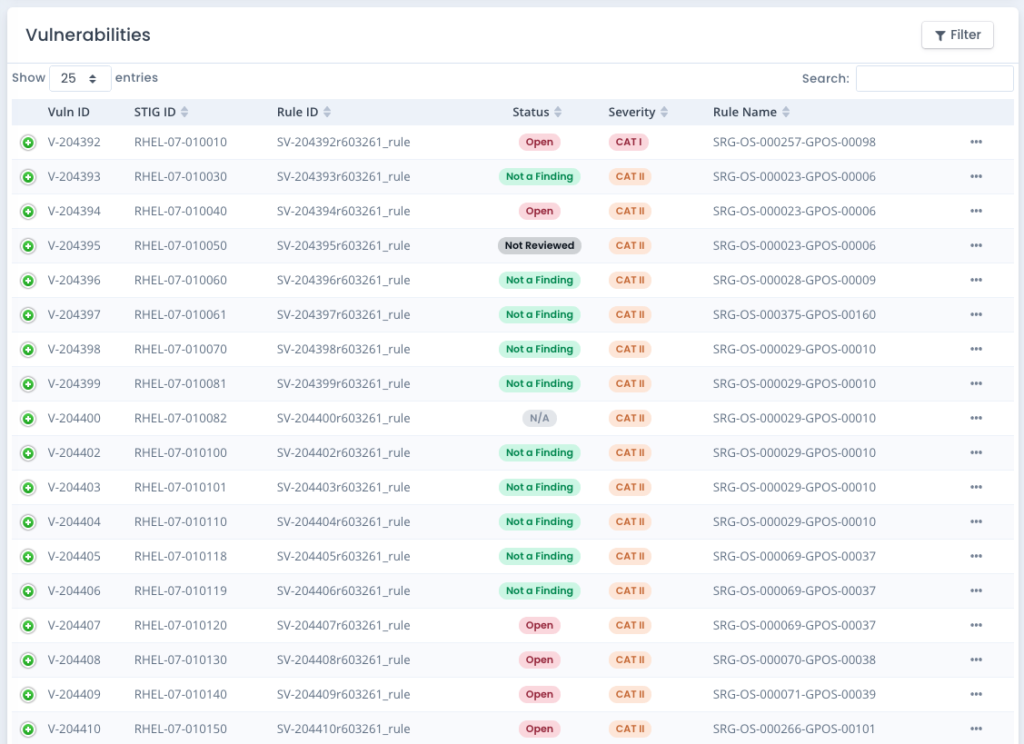
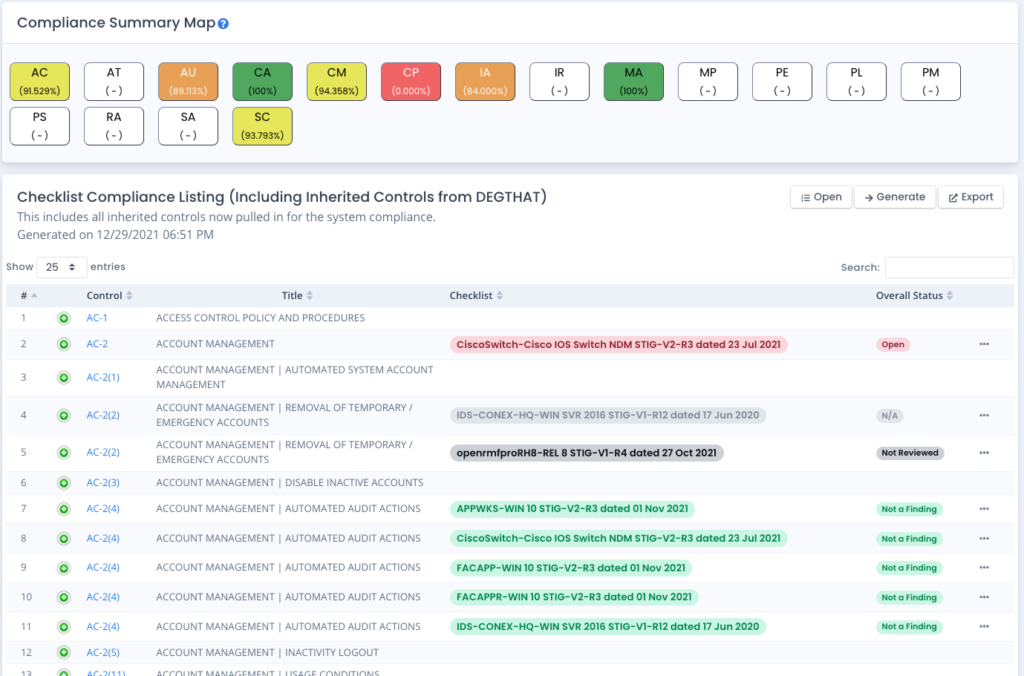
Manage All System Package Data
Track all STIG Checklists, Patch Vulnerabilities, Software and Hardware, PPSM, Tailoring, Overlays, and more from a single web-based application.
- Store all STIG checklists, convert SCAP Scans and Audit Compliance Scans into checklists, and version changes automatically
- Track open Patch Vulnerabilities as well as your open items for current status as well as historically through the life of the system package
- Track other Vulnerability data (software scans, container scans, etc.) for current status as well as historically through the life of the system package
- Apply Compliance Overlays and setup your Tailored NIST Controls to the sub-control level
- Link your POAM, Test Plan, SSP, SAR, and RAR as well as Mitigation Statements to your live data
- Track Milestone Events, download and setup in your calendar application
- Keep all your System Package data in one spot, where it is under configuration management and audited for changes and security
- Download a Summary Presentation (PPTX) from your source of truth in seconds